Step0:
Enable Virtualization Technology in BIOS
Step1:
Install CentOS5.7 (Final) with GNOME. This is host machine
Step2:
Install VirtualBox on host machine
Step3:
Create a virtual machine with the following settings:
System --> Motherboard:
Chipset: ICH9
Extended Features: Enable IO APIC, Hardware clock in UTC time
Storage:
Controller: SCSI
Network:
Attached to: Bridged Adapter
Step4:
Install CentOS5.7 (Final) on virtual machine which is created at Step3
Step5:
Copy file *.vdi to another directory (* = file name)
Execute the following command to change uuid of *.vdi file.
VBoxManage internalcommands sethduuid /path/to/*.vdi
Step6:
Create another virtual machine with copied hard disk.
Step7:
Start new virtual machine
Step8:
Repeat Step5~7 if you want to clone more virtual machine.
Tuesday, October 15, 2013
Monday, October 14, 2013
How to install GNOME desktop from DVD
Source: http://superuser.com/questions/432000/how-to-install-gnome-desktop-from-dvd-on-centos-6-using-the-command-line
As you have installed CentOS in VirtualBox, and as I understand, while installing you haven't choose X window system, so you are getting black screen with white cursor blinking.
Now what you can do is, install X Window System. If you have internet access in VirtualBox then you can try
yum groupinstall "X Window System"
This will use your internet connection to download the packages and install on system.
If you don't have internet access in VirtualBox then I will suggest you to mount the CD ROM in a virtual machine and install using that.
First of all you need to create a mount point and mount the Installation Media
mkdir /medir/cdr
mount /dev/cdrom /media/cdr
Now you have to create a local repository in /etc/yum.repo.d/
cd /etc/yum.repo.d/
vi local.repo
In this file write
[installation Media]
Name="Centos Local Installation"
baseurl=file:///media/cdr
enabled=1
gpgcheck=0
Now you can install the X Window system using
yum groupinstall "X Window System" "GNOME Desktop Environment"
As you have installed CentOS in VirtualBox, and as I understand, while installing you haven't choose X window system, so you are getting black screen with white cursor blinking.
Now what you can do is, install X Window System. If you have internet access in VirtualBox then you can try
yum groupinstall "X Window System"
This will use your internet connection to download the packages and install on system.
If you don't have internet access in VirtualBox then I will suggest you to mount the CD ROM in a virtual machine and install using that.
First of all you need to create a mount point and mount the Installation Media
mkdir /medir/cdr
mount /dev/cdrom /media/cdr
Now you have to create a local repository in /etc/yum.repo.d/
cd /etc/yum.repo.d/
vi local.repo
In this file write
[installation Media]
Name="Centos Local Installation"
baseurl=file:///media/cdr
enabled=1
gpgcheck=0
Now you can install the X Window system using
yum groupinstall "X Window System" "GNOME Desktop Environment"
Sunday, September 8, 2013
OpenSSL is written by monkeys
Source: http://www.peereboom.us/assl/assl/html/openssl.html
I know it sounds harsh but lets investigate the facts.
create_server
create_client
At home I sit in the shower and cry a little, WAIT, is that blood???
I know it sounds harsh but lets investigate the facts.
First lets get out of the way who is complaining. Hi, I am Marco Peereboom and I write open source code for fun. I have been involved in several projects and the google will tell you which ones. I am by no stretch of the imagination a great programmer but I have been around and I have written a couple of things.
Recently I got involved in writing some code that requires secure communications and I figured that there was no better way to get cranking than to use a well known and widely used library. Essentially my problem boils down to this:
- Write an application that provides CA (Certificate Authority) services.
- Store all certificates in an LDAP tree.
The debate is not about the merit of this idea but this is where the journey started. It sounded simple enough so off to the web looking for documentation and code snippets, this is obviously going to be a walk in the park since all these problems have been solved before.
After messing around with this code for about a month I decided to write this up for the tubes in the hope that I can save some souls. I have come to the conclusion that OpenSSL is equivalent to monkeys throwing feces at the wall. It is, bar none, the worst library I have ever worked with. I can not believe that the internet is running on such a ridiculous complex and gratuitously stupid piece of code. Since circa 1998 the whole world has been trusting their secure communications to this impenetrable morass that calls itself the "OpenSSL" project. I bet that the doctors that work on that shitshow can not prescribe anything useful either!
Day 1:
Hmmm can't find a whole bunch of code at all. What I do find doesn't help me with my CA problem at all. Everything I do find is basically a whole bunch of HOWTOS written by people who don't seem to grasp the underlying problems. They mean well but really hurt the community as a whole by providing recipes for disaster. Alright no problem off to Barnes & Nobles and lets see what we can find.
Crap! Nothing really. I found 2 books and they were mostly about using the command line tool. One had some code examples but nothing advanced at all. Apparently people only seem to care about using openssl "the tool".
I had peeked at the code and it gave me vertigo so I stepped away from it. Anyway at this point I was starting to suspect that this might not be as easy as I had hopped. Time to go home anyway and drink a cold one.
Day 2:
Alright screw it! I'll look at the damn code; I mean all books and examples on the web use it. At least it'll point me to what functions I need to call and I'll be able to find those in the fine documentation. First I obviously need to figure out how to use openssl "the tool".
8 hours later...
Phew I got something that works after reading endless HOWTOS, specs and postings on the tubes. The documentation was, how does one say that? Really really bad! Let me share with you my labor of love. I created 3 scripts to illustrate my problem of having a CA that signs client and server certificates.
- create_ca, this script creates the CA
- create_server, this script creates a server certificate and keys
- create_client, this script creates a client certificate and keys
#/bin/sh
mkdir -p ca/private
chmod 700 ca/private
openssl req -x509 -days 3650 -newkey rsa:1024 -keyout ca/private/ca.key -out ca/ca.crt
create_server
#/bin/sh
mkdir -p server/private
chmod 700 server/private
openssl genrsa -out server/private/server.key 1024
openssl req -new -key server/private/server.key -out server/server.csr
create_client
#/bin/sh
mkdir -p client/private
chmod 700 client/private
openssl genrsa -out client/private/client.key 1024
openssl req -new -key client/private/client.key -out client/client.csr
enough for a day. Time to go home.
Day 3: Alright, that openssl "the tool" stuff out of the way lets dig into that code. Hmmm, where is main? How does it call the individual modules? Random camel capitalization mixed with underscores wow! Ugh MAIN macro, great. *WASH_Eyes_outWith_soap*
Ok we are going to need some serious tags to be able to navigate this morass. After a couple of hours of digging through the code I kind of get the hang of it (thanks vim!). Now it is time to start walking this code backwards and see if I can generate a CA without having to use openssl "the tool". A few more hours go by and the incomplete man pages, no man pages, poorly written man pages really start to wear on me. No help from google, bing, yahoo etc. The documentation is simply non-existent and what does exist is outdated and does not match reality. Screw it, I am going home!
Day 4:
I start writing some code based on what I find in openssl "the tool". Progress is painfully slow due to the embarrassingly bad style, indentation and don't get me started about impenetrable #ifdef goo. Speaking of #ifdefs I saw several dangling ones that would eat an instruction; e.g.
#ifdef (OMG)
if (moo) {
...
} else
#endif /* OMG */
yeah();
This is actually the pretty version. The one I ran into was over a couple hundred lines of code with indentation that makes a grown man cry. Lets also get one other thing out of the way. If you think if (moo)
{
dome_something_dumb();
}
else
{
or_not();
}
or if ( moo)
{
blah();
}
if (bad)
goto err;
...
if (0) {
err:
do_something_horrible();
}
is readable I suggest you visit an optometrist. Possibly even a proctologist. Lets look at a few real examples if ((OBJ_obj2nid(obj) == NID_pkcs9_emailAddress) &&
(str->type != V_ASN1_IA5STRING))
{
BIO_printf(bio_err,"\nemailAddress type needs to be of type IA5STRING\n");
goto err;
}
if ((str->type != V_ASN1_BMPSTRING) && (str->type != V_ASN1_UTF8STRING))
{
j=ASN1_PRINTABLE_type(str->data,str->length);
if ( ((j == V_ASN1_T61STRING) &&
(str->type != V_ASN1_T61STRING)) ||
((j == V_ASN1_IA5STRING) &&
(str->type == V_ASN1_PRINTABLESTRING)))
{
BIO_printf(bio_err,"\nThe string contains characters that are illegal for the ASN.1 type\n");
goto err;
}
}
Here is an example of a function stack; vim to the rescue! if (!SSL_CTX_use_certificate_file(ctx, "server/server.crt", SSL_FILETYPE_PEM))
ctrl ]
...
else if (type == SSL_FILETYPE_PEM)
{
j=ERR_R_PEM_LIB;
x=PEM_read_bio_X509(in,NULL,ctx->default_passwd_callback,ctx->default_passwd_callback_userdata);
ctrl ]
...
#define PEM_read_bio_X509(bp,x,cb,u) (X509 *)PEM_ASN1_read_bio( \
(char *(*)())d2i_X509,PEM_STRING_X509,bp,(char **)x,cb,u)
ctrl ]
...
if (!PEM_bytes_read_bio(&data, &len, NULL, name, bp, cb, u))
return NULL;
ctrl ]
...
if (!PEM_read_bio(bp,&nm,&header,&data,&len)) {
ctrl ]
...
i=BIO_gets(bp,buf,254);
ctrl ]
...
i=b->method->bgets(b,in,inl);
That spanned 5 files, 6 indirections and all that to open and fgets the contents of a file. And we still are doing an indirect call. All this work and jumping around when all I wanted is to have a function that can translate a PEM (NOT in a file!!!) cert into a X509 structure. But between the million or so functions nothing handy like that exists; or so I suspect but since there are no docs I really have to guess. I can't rob you guys from this gem either:#ifndef OPENSSL_NO_STDIO
/*!
* Load CA certs from a file into a ::STACK. Note that it is somewhat misnamed;
* it doesn't really have anything to do with clients (except that a common use
* for a stack of CAs is to send it to the client). Actually, it doesn't have
* much to do with CAs, either, since it will load any old cert.
* \param file the file containing one or more certs.
* \return a ::STACK containing the certs.
*/
STACK_OF(X509_NAME) *SSL_load_client_CA_file(const char *file)
{
BIO *in;
X509 *x=NULL;
X509_NAME *xn=NULL;
STACK_OF(X509_NAME) *ret = NULL,*sk;
sk=sk_X509_NAME_new(xname_cmp);
in=BIO_new(BIO_s_file_internal());
if ((sk == NULL) || (in == NULL))
{
SSLerr(SSL_F_SSL_LOAD_CLIENT_CA_FILE,ERR_R_MALLOC_FAILURE);
goto err;
}
if (!BIO_read_filename(in,file))
goto err;
for (;;)
{
if (PEM_read_bio_X509(in,&x,NULL,NULL) == NULL)
break;
if (ret == NULL)
{
ret = sk_X509_NAME_new_null();
if (ret == NULL)
{
SSLerr(SSL_F_SSL_LOAD_CLIENT_CA_FILE,ERR_R_MALLOC_FAILURE);
goto err;
}
}
if ((xn=X509_get_subject_name(x)) == NULL) goto err;
/* check for duplicates */
xn=X509_NAME_dup(xn);
if (xn == NULL) goto err;
if (sk_X509_NAME_find(sk,xn) >= 0)
X509_NAME_free(xn);
else
{
sk_X509_NAME_push(sk,xn);
sk_X509_NAME_push(ret,xn);
}
}
if (0)
{
err:
if (ret != NULL) sk_X509_NAME_pop_free(ret,X509_NAME_free);
ret=NULL;
}
if (sk != NULL) sk_X509_NAME_free(sk);
if (in != NULL) BIO_free(in);
if (x != NULL) X509_free(x);
if (ret != NULL)
ERR_clear_error();
return(ret);
}
#endif
Wow! that one does it all! unreadable, lots of indirection and no clear direction as to what the function is trying to achieve. Got to love the if (0) construct! I mean that obviously wins all the beauty, aesthetics & NIH awards. You have to be overjoyed to know that this type of code runs a lot of our "secure" internet.
Silly me to just want to have a function to read certs from LDAP or memory so that I can write the LDAP code myself. Not much code got written, I need to go home and go into some sort of drunken stooper.
Day 5:
This is starting to piss me off! Armed with a fresh headache I get with the coding part. After a couple of hours of reading and rereading some openssl "the tool" code I came up with this:
int
create_ca(char *retstr, size_t retlen)
{
int rv = 1;
int days = 365 * 10;
char *password = NULL;
EVP_PKEY pkey, *tmppkey = NULL;
BIGNUM bn;
RSA *rsa = NULL;
X509_REQ *req = NULL;
X509_NAME *subj;
X509 *x509 = NULL;
BIO *out = NULL;
/* generate private key */
if ((rsa = RSA_new()) == NULL)
ERROR_OUT(ERR_SSL, done);
bzero(&bn, sizeof bn);
if (BN_set_word(&bn, 0x10001) == 0)
ERROR_OUT(ERR_SSL, done);
if (RSA_generate_key_ex(rsa, 1024, &bn, NULL) == 0)
ERROR_OUT(ERR_SSL, done);
bzero(&pkey, sizeof pkey);
if (EVP_PKEY_assign_RSA(&pkey, rsa) == 0)
ERROR_OUT(ERR_SSL, done);
/* setup req for certificate */
if ((req = X509_REQ_new()) == NULL)
ERROR_OUT(ERR_SSL, done);
if (X509_REQ_set_version(req, 0) == 0)
ERROR_OUT(ERR_SSL, done);
subj = X509_REQ_get_subject_name(req);
if (validate_canew(subj, &password)) {
snprintf(last_error, sizeof last_error,
"validate_canew failed");
ERROR_OUT(ERR_OWN, done);
}
/* set public key to req */
if (X509_REQ_set_pubkey(req, &pkey) == 0)
ERROR_OUT(ERR_SSL, done);
/* generate 509 cert */
if ((x509 = X509_new()) == NULL)
ERROR_OUT(ERR_SSL, done);
bzero(&bn, sizeof bn);
if (BN_pseudo_rand(&bn, 64 /* bits */, 0, 0) == 0)
ERROR_OUT(ERR_SSL, done);
if (BN_to_ASN1_INTEGER(&bn, X509_get_serialNumber(x509)) == 0)
ERROR_OUT(ERR_SSL, done);
if (X509_set_issuer_name(x509, X509_REQ_get_subject_name(req)) == 0)
ERROR_OUT(ERR_SSL, done);
if (X509_gmtime_adj(X509_get_notBefore(x509), 0) == 0)
ERROR_OUT(ERR_SSL, done);
if (days == 0) {
snprintf(last_error, sizeof last_error,
"not enough days for certificate");
ERROR_OUT(ERR_OWN, done);
}
days *= 60 * 60 * 24;
if (X509_gmtime_adj(X509_get_notAfter(x509), days) == 0)
ERROR_OUT(ERR_SSL, done);
if (X509_set_subject_name(x509, X509_REQ_get_subject_name(req)) == 0)
ERROR_OUT(ERR_SSL, done);
if ((tmppkey = X509_REQ_get_pubkey(req)) == NULL)
ERROR_OUT(ERR_SSL, done);
if (X509_set_pubkey(x509, tmppkey) == 0)
ERROR_OUT(ERR_SSL, done);
if (X509_sign(x509, &pkey, EVP_sha1()) == 0)
ERROR_OUT(ERR_SSL, done);
/* write private key */
out = BIO_new(BIO_s_file());
if (BIO_write_filename(out, CA_PKEY) <= 0)
ERROR_OUT(ERR_SSL, done);
if (chmod(CA_PKEY, S_IRWXU))
ERROR_OUT(ERR_LIBC, done);
if (PEM_write_bio_PrivateKey(out, &pkey, EVP_des_ede3_cbc(), NULL, 0,
NULL, password) == 0)
ERROR_OUT(ERR_SSL, done);
BIO_free_all(out);
/* write cert */
out = BIO_new(BIO_s_file());
if (BIO_write_filename(out, CA_CERT) <= 0)
ERROR_OUT(ERR_SSL, done);
if (PEM_write_bio_X509(out, x509) == 0)
ERROR_OUT(ERR_SSL, done);
BIO_free_all(out);
rv = 0;
done:
if (tmppkey)
EVP_PKEY_free(tmppkey);
if (x509)
X509_free(x509);
if (req)
X509_REQ_free(req);
if (rsa)
RSA_free(rsa);
return (rv);
}
As you can see I create an awful mechanism to at least get some sort of usable fault stack to trace errors. Here is the macro in its full horror:/* errors */
#define ERR_LIBC (0)
#define ERR_SSL (1)
#define ERR_OWN (2)
#define ERROR_OUT(e, g) do { push_error(__FILE__, __FUNCTION__, __LINE__, e); goto g; } while(0)
Dear $DEITY I beg your forgiveness for I have sinned.
Let me show the other bits to make this work just for completions sake and to hope I can help another lost soul that has to put up with this poo. The functions that play with this garbage:
char *
geterror(int et)
{
char *es;
switch (et) {
case ERR_LIBC:
strlcpy(last_error, strerror(errno), sizeof last_error);
break;
case ERR_SSL:
es = (char *)ERR_lib_error_string(ERR_get_error());
if (es)
strlcpy(last_error, es, sizeof last_error);
else
strlcpy(last_error, "unknown SSL error",
sizeof last_error);
break;
default:
strlcpy(last_error, "unknown error", sizeof last_error);
/* FALLTHROUGH */
case ERR_OWN:
break;
}
return (last_error);
}
void
push_error(char *file, char *func, int line, int et)
{
struct error *ce;
if ((ce = calloc(1, sizeof *ce)) == NULL)
fatal("push_error ce");
if ((ce->file = strdup(file)) == NULL)
fatal("push_error ce->file");
if ((ce->func = strdup(func)) == NULL)
fatal("push_error ce->func");
if ((ce->errstr = strdup(geterror(et))) == NULL)
fatal("push_error ce->errstr");
ce->line = line;
SLIST_INSERT_HEAD(&ces, ce, dlink);
}
Here are the remaining utility functions to make it all "work":int
cert_find_put(char *entry, X509_NAME *subj, ssize_t min, ssize_t max)
{
struct valnode *v;
int rv = 1;
v = find_valtree(entry);
if (v && v->length > 0) {
if (min != -1 && v->length < min) {
snprintf(last_error, sizeof last_error,
"%s minimum constraint not met %lu < %lu",
entry, v->length, min);
ERROR_OUT(ERR_OWN, done);
}
if (max != -1 && v->length > max) {
snprintf(last_error, sizeof last_error,
"%s maximum constraint not met %lu > %lu",
entry, v->length, max);
ERROR_OUT(ERR_OWN, done);
}
if (X509_NAME_add_entry_by_txt(subj, entry, MBSTRING_ASC,
v->value, -1, -1, 0) == 0)
ERROR_OUT(ERR_SSL, done);
} else {
log_debug("cert_find_put: %s not found", entry);
goto done;
}
rv = 0;
done:
return (rv);
}
int
validate_canew(X509_NAME *subj, char **pwd)
{
struct valnode *password, *password2;
int rv = 1;
password = find_valtree("password");
password2 = find_valtree("password2");
if (password && password2) {
if (strcmp(password->value, password2->value) ||
password->length == 0) {
snprintf(last_error, sizeof last_error,
"invalid password");
ERROR_OUT(ERR_OWN, done);
}
*pwd = password->value;
}
if (password == NULL && password2 == NULL) {
snprintf(last_error, sizeof last_error,
"password can't be NULL");
ERROR_OUT(ERR_OWN, done);
}
if (cert_find_put("C", subj, 2, 2)) {
snprintf(last_error, sizeof last_error,
"invalid country");
ERROR_OUT(ERR_OWN, done);
}
cert_find_put("ST", subj, -1, -1);
cert_find_put("L", subj, -1, -1);
cert_find_put("O", subj, -1, -1);
cert_find_put("OU", subj, -1, -1);
cert_find_put("CN", subj, -1, -1);
cert_find_put("emailAddress", subj, -1, -1);
rv = 0;
done:
return (rv);
}
Jubilation! We have a CA OMG!!!oneONE!!!111~ Time to go home!At home I sit in the shower and cry a little, WAIT, is that blood???
Day 6:
I'll get to writing stuff into LDAP later. I need to work on something else for a while. So next up, a client/server app that negotiates SSL/TLS. First I try various examples on the net.
Big bag of FAIL
Well, then we'll look at the man pages, I mean they totally come with an example!
Second big bag of FAIL
Farting around with crap I found on the net + example + a lot of time.
Third big bag of FAIL
Enough, I am going home.
Day 7:
Alright, time to go back into my by now favorite piece of code! openssl "the tool" has s_server and s_client and if you push the buttons it sort of seems to work. These are the magic commands I came up with:
openssl s_server -CAfile ca/ca.crt -cert server/server.crt -key server/private/server.key -Verify 1
openssl s_client -CAfile ca/ca.crt -cert client/client.crt -key client/private/client.key
That connects over SSL/TLS according to it and it seemed ok in tcpdump as well. So lets start coding! I'll present you here with my test code, again I am hoping to do other folks a favor and hope that a few murders can be averted. First up the server:#include <stdio.h>
#include <stdlib.h>
#include <err.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <netinet/in.h>
#include "openssl/bio.h"
#include "openssl/ssl.h"
#include "openssl/err.h"
void
fatalx(char *s)
{
ERR_print_errors_fp(stderr);
errx(1, s);
}
int
main(int argc, char *argv[])
{
SSL_CTX *ctx;
BIO *sbio;
SSL *ssl;
int sock, s, r, val = -1;
struct sockaddr_in sin;
SSL_load_error_strings();
OpenSSL_add_ssl_algorithms();
ctx = SSL_CTX_new(SSLv23_server_method());
if (ctx == NULL)
fatalx("ctx");
if (!SSL_CTX_load_verify_locations(ctx, "ca/ca.crt", NULL))
fatalx("verify");
SSL_CTX_set_client_CA_list(ctx, SSL_load_client_CA_file("ca/ca.crt"));
if (!SSL_CTX_use_certificate_file(ctx, "server/server.crt", SSL_FILETYPE_PEM))
fatalx("cert");
if (!SSL_CTX_use_PrivateKey_file(ctx, "server/private/server.key", SSL_FILETYPE_PEM))
fatalx("key");
if (!SSL_CTX_check_private_key(ctx))
fatalx("cert/key");
SSL_CTX_set_mode(ctx, SSL_MODE_AUTO_RETRY);
SSL_CTX_set_verify(ctx, SSL_VERIFY_PEER | SSL_VERIFY_FAIL_IF_NO_PEER_CERT, NULL);
SSL_CTX_set_verify_depth(ctx, 1);
/* setup socket */
if ((sock = socket(AF_INET, SOCK_STREAM, 0)) == -1)
err(1, "socket");
bzero(&sin, sizeof sin);
sin.sin_addr.s_addr = INADDR_ANY;
sin.sin_family = AF_INET;
sin.sin_port = htons(4433);
setsockopt(sock, SOL_SOCKET, SO_REUSEADDR, &val, sizeof val);
if (bind(sock, (struct sockaddr *)&sin, sizeof sin) == -1)
err(1, "bind");
listen(sock, 0);
for (;;) {
if ((s = accept(sock, 0, 0)) == -1)
err(1, "accept");
sbio = BIO_new_socket(s, BIO_NOCLOSE);
ssl = SSL_new(ctx);
SSL_set_bio(ssl, sbio, sbio);
if ((r = SSL_accept(ssl)) == -1)
fatalx("SSL_accept");
printf("handle it!\n");
}
return (0);
}
and the client:#include <stdio.h>
#include <stdlib.h>
#include <err.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <netinet/in.h>
#include <netdb.h>
#include "openssl/bio.h"
#include "openssl/ssl.h"
#include "openssl/err.h"
void
fatalx(char *s)
{
ERR_print_errors_fp(stderr);
errx(1, s);
}
int
main(int argc, char *argv[])
{
SSL_CTX *ctx;
BIO *sbio;
SSL *ssl;
struct sockaddr_in addr;
struct hostent *hp;
int sock;
SSL_load_error_strings();
OpenSSL_add_ssl_algorithms();
ctx = SSL_CTX_new(SSLv23_client_method());
if (ctx == NULL)
fatalx("ctx");
if (!SSL_CTX_load_verify_locations(ctx, "ca/ca.crt", NULL))
fatalx("verify");
if (!SSL_CTX_use_certificate_file(ctx, "client/client.crt", SSL_FILETYPE_PEM))
fatalx("cert");
if (!SSL_CTX_use_PrivateKey_file(ctx, "client/private/client.key", SSL_FILETYPE_PEM))
fatalx("key");
if (!SSL_CTX_check_private_key(ctx))
fatalx("cert/key");
SSL_CTX_set_mode(ctx, SSL_MODE_AUTO_RETRY);
SSL_CTX_set_verify(ctx, SSL_VERIFY_PEER, NULL);
SSL_CTX_set_verify_depth(ctx, 1);
/* setup connection */
if ((hp = gethostbyname("localhost")) == NULL)
err(1, "gethostbyname");
bzero(&addr, sizeof addr);
addr.sin_addr = *(struct in_addr *)hp->h_addr_list[0];
addr.sin_family = AF_INET;
addr.sin_port = htons(4433);
if ((sock = socket(AF_INET, SOCK_STREAM, 0)) == -1)
err(1, "socket");
if (connect(sock, (struct sockaddr *)&addr, sizeof addr) == -1)
err(1, "connect");
/* go do ssl magic */
ssl = SSL_new(ctx);
sbio = BIO_new_socket(sock, BIO_NOCLOSE);
SSL_set_bio(ssl, sbio, sbio);
if (SSL_connect(ssl) <= 0)
fatalx("SSL_connect");
if (SSL_get_verify_result(ssl) != X509_V_OK)
fatalx("cert");
return (0);
}
Not my best work but it works and someone might be helped by this. Going home!
Day 8:
Looking some more on how to make those damned files work within LDAP. Between meetings and other lame things I gave up and wrote this rant instead. I'll continue to update this as I make more progress. I shall overcome the excrement flinging ape that is OpenSSL.
The opinions of the author expressed herein do not necessarily state or reflect those of anyone else.
Opinion and code © 2009 Marco Peereboom.
Code snippets from the OpenSSL project are © 1998-2009 The OpenSSL Project.
Opinion and code © 2009 Marco Peereboom.
Code snippets from the OpenSSL project are © 1998-2009 The OpenSSL Project.
$assl: openssl.html,v 1.3 2009/08/24 18:45:53 marco Exp $
Friday, September 6, 2013
BASH notes
yesterday=$(date --date='1 day ago' +"%Y%m%d")
# comment in bash shell
: <<'END' comments' here and here END
PERL notes
# get YMD sub today() { my @t = localtime(time); my $ymd = sprintf("%02d%02d%02d", $t[5] + 1900, $t[4] + 1, $t[3]); return $ymd; }
# Install perl module to custom directory
perl Makefile.PL INSTALL_BASE=/home/mgsys/perl5or
perl Makefile.PL PREFIX=/home/mgsys/perl5
Wednesday, August 21, 2013
Facebook founder Zuckerberg hacked to highlight bug
Facebook founder Zuckerberg hacked to highlight bug
By
Joe Miller BBC News

A
screenshot of the message left on Mark Zuckerberg's wall
A
Palestinian programmer has highlighted a flaw in Facebook's security
system by posting a message on Mark Zuckerberg's private page.
Khalil
Shreateh used a vulnerability he discovered to hack the account of
the Facebook founder and raise the alarm.
Mr
Shreateh said he had tried to use Facebook's White Hat scheme, which
offers a monetary reward for reporting vulnerabilities, but had been
ignored.
Facebook
said it had fixed the fault but would not be paying Mr Shreateh.
Mr
Shreateh found a security breach that allowed Facebook users to post
messages on the private "walls" of people who had not
approved them as "friends", overriding the site's privacy
features.
'Not
a bug'
He
wrote to Facebook's White Hat team to warn them of the glitch,
providing basic details of his discovery.
After
a short exchange with the team, Mr Shreateh received an email saying:
"I am sorry this is not a bug".
Following
this rebuttal, Mr Shreateh exploited the bug to post a message on Mr
Zuckerberg's page.
In
the post, Mr Shreateh, whose first language is Arabic, said he was
"sorry for breaking your privacy and post to your wall" but
that he had "no other choice" after being ignored by
Facebook's security team.
An
engineer on Facebook's security team, Matt Jones, posted
a public explanation saying
that although Mr Shreateh's original email should have been followed
up, the way he had reported the bug had violated the site's
"responsible disclosure policy".
He
added that as Mr Shreateh had highlighted the bug "using the
accounts of real people without their permission", he would not
qualify for a payout.
Thursday, August 8, 2013
PHP display images in a directory
<?
ini_set("memory_limit","256M");
if (!isset($_POST["id"])) {
$id = 0;
} else {
$id = $_POST["id"];
}
$lines = file("img.txt", FILE_IGNORE_NEW_LINES);
echo "<br /><br /><center><img src='$lines[$id]'/><br /></center>";
$id++;
echo '<form action="get_image.php" method="post">';
echo '<center>';
echo "id: <input type=\"text\" name=\"id\" value=\"$id\"><br />";
echo '<input type="submit">';
echo '</center>';
echo '</form>';
?>
File img.txt:
4342342.png
8539750.png
3257398.png
ini_set("memory_limit","256M");
if (!isset($_POST["id"])) {
$id = 0;
} else {
$id = $_POST["id"];
}
$lines = file("img.txt", FILE_IGNORE_NEW_LINES);
echo "<br /><br /><center><img src='$lines[$id]'/><br /></center>";
$id++;
echo '<form action="get_image.php" method="post">';
echo '<center>';
echo "id: <input type=\"text\" name=\"id\" value=\"$id\"><br />";
echo '<input type="submit">';
echo '</center>';
echo '</form>';
?>
File img.txt:
4342342.png
8539750.png
3257398.png
Tuesday, August 6, 2013
BASH Shell Color
Source: http://www.cyberciti.biz/faq/bash-shell-change-the-color-of-my-shell-prompt-under-linux-or-unix/
BASH Shell: Change The Color of My Shell Prompt Under Linux or UNIX
in BASH SHELL, LINUX, UNIX
How do I change the color of my shell prompt under Linux or Unix operating systems?
You can change the color of your shell prompt to impress your friend or to make your own life quite easy while working at the command prompt. BASH shell is the default under Linux and Apple OS X. Your current prompt setting is stored in a shell variable called PS1. There are other variables too, like PS2, PS3 and PS4.
Bash displays the primary prompt PS1 when it is ready to read a command, and the secondary prompt PS2 when it needs more input to complete a command. Bash allows these prompt strings to be customized by inserting a number of backslash-escaped special characters.
Where,
You can change the color of your shell prompt to impress your friend or to make your own life quite easy while working at the command prompt. BASH shell is the default under Linux and Apple OS X. Your current prompt setting is stored in a shell variable called PS1. There are other variables too, like PS2, PS3 and PS4.
| Tutorial details | |
|---|---|
| Difficulty | Easy (rss) |
| Root privileges | No |
| Requirements | Bash |
| Estimated completion time | N/A |
Bash displays the primary prompt PS1 when it is ready to read a command, and the secondary prompt PS2 when it needs more input to complete a command. Bash allows these prompt strings to be customized by inserting a number of backslash-escaped special characters.
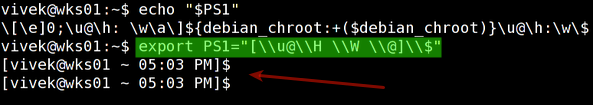
Task: Display current BASH prompt (PS1)
Use the echo command to display current BASH prompt:
Sample outputs:
$ echo $PS1Sample outputs:
[\\u@\h \\W]\\$
Here is another output from my Debian based system:
Sample outputs:
$ echo $PS1Sample outputs:
\[\e]0;\u@\h: \w\a\]${debian_chroot:+($debian_chroot)}\u@\h:\w\$
By default the command prompt is set to [\u@\h \W]\$. The backslash-escaped special characters are decoded as follows:
- \u: Display the current username .
- \h: Display the hostname
- \W: Print the base of current working directory.
- \$: Display # (indicates root user) if the effective UID is 0, otherwise display a $.
Task: Modify current BASH prompt
Use the export command to setup a new shell prompt:
Sample outputs:
$ export PS1="[\\u@\\H \\W \\@]\\$"Sample outputs:
Where,
- \H: Display FQDN hostname.
- \@: Display current time in 12-hour am/pm format
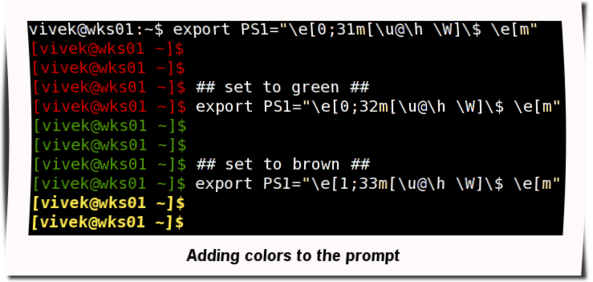
Task: Add colors to the prompt
To add colors to the shell prompt use the following export command syntax:
'\e[x;ym $PS1 \e[m'
Where,
'\e[x;ym $PS1 \e[m'
Where,
- \e[ : Start color scheme.
- x;y : Color pair to use (x;y)
- $PS1 : Your shell prompt variable.
- \e[m : Stop color scheme.
To set a red color prompt, type the following command:
Sample outputs:
$ export PS1="\e[0;31m[\u@\h \W]\$ \e[m "Sample outputs:
A list of color codes
| Color | Code |
| Black | 0;30 |
| Blue | 0;34 |
| Green | 0;32 |
| Cyan | 0;36 |
| Red | 0;31 |
| Purple | 0;35 |
| Brown | 0;33 |
| Blue | 0;34 |
| Green | 0;32 |
| Cyan | 0;36 |
| Red | 0;31 |
| Purple | 0;35 |
| Brown | 0;33 |
Note: You need to replace digit 0 with 1 to get light color version.
Task: How do I make the prompt setting permanent?
Your new shell prompt setting set by $PS1 is temporary i.e. when you logout setting will be lost. To have it set every time you login to your workstation add above export command to your $HOME/.bash_profile file or $HOME/.bashrc file.
OR
Append the following line:
Save and close the file.
$ cd
$ vi .bash_profileOR
$ vi $HOME/.bashrcAppend the following line:
export PS1="\e[0;31m[\u@\h \W]\$ \e[m"Save and close the file.
Say hello to tput command
You can also use tput command to set terminal and modify the prompt settings. For example, to display RED color prompt using a tput:
export PS1="\[$(tput setaf 1)\]\u@\h:\w $ \[$(tput sgr0)\]"A list of handy tput command line options
- tput bold - Bold effect
- tput rev - Display inverse colors
- tput sgr0 - Reset everything
- tput setaf {CODE}- Set foreground color, see color {CODE} table below for more information.
- tput setab {CODE}- Set background color, see color {CODE} table below for more information.
Various color codes for the tput command
| Color {code} | Color |
| 0 | Black |
| 1 | Red |
| 2 | Green |
| 3 | Yellow |
| 4 | Blue |
| 5 | Magenta |
| 6 | Cyan |
| 7 | White |
RECOMMEND READINGS
- HowTo: Change or setup your bash custom prompt (PS1) - This tutorial explains how-to customizing a bash shell to get a good looking prompt, configure the appearance of the terminal and apply themes using bashish package.
- man page - bash
Subscribe to:
Posts (Atom)